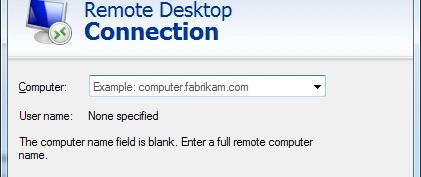
Swan Vector APT Attacks: DLL Implants Threaten Asia’s Education & Engineering
Overview of Swan Vector APT Swan Vector APT is a newly surfaced advanced persistent threat group that has been actively exploiting human trust vectors to infiltrate organizations in Taiwan and…