Table of Contents
A newly uncovered threat campaign shows how attackers are using a PowerShell-Based Loader Deploys Remcos RAT through fileless attack techniques, bypassing traditional AV and EDR controls. The malware resides entirely in memory, leveraging living-off-the-land binaries (LOLBins) and obfuscated PowerShell to maintain stealth and persistence.
Remcos (Remote Control & Surveillance) is a commercially available Remote Access Trojan widely used by cybercriminals for surveillance, credential theft, and persistence in enterprise environments.
This highlights the importance of understanding how the PowerShell-Based Loader Deploys Remcos RAT operates within enterprise environments.
This campaign demonstrates advanced evasion and highlights the growing trend of fileless malware that evades endpoint detection by avoiding disk writes entirely.
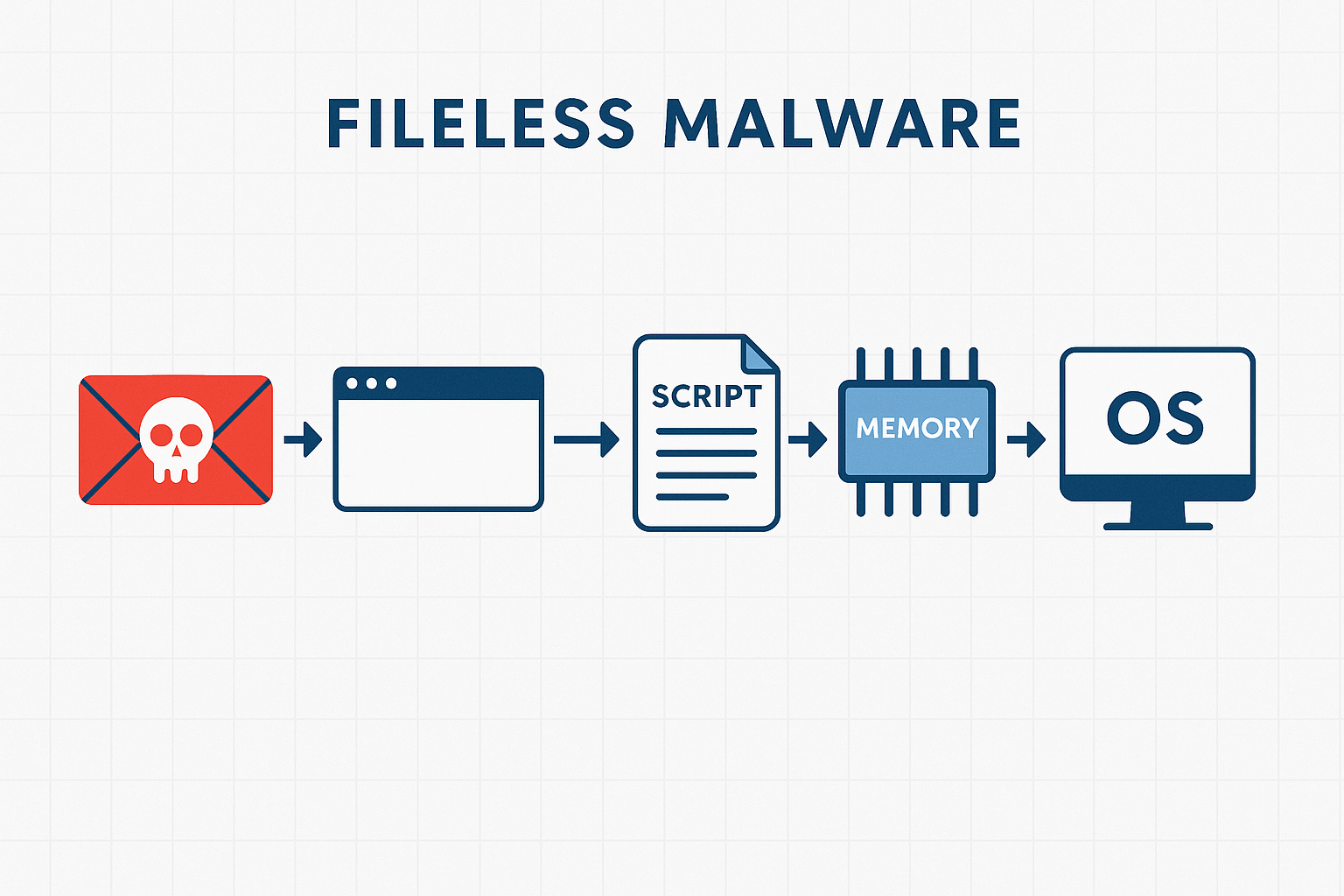
How the Fileless Attack Works
The attack chain follows a typical malspam or drive-by download pattern but diverges by never writing persistent files to disk.
🔗 Infection Vector
- Phishing email with a malicious link or weaponized attachment (e.g., Excel macro or PDF exploit)
- Triggered payload invokes PowerShell directly, often via LOLBins like
mshta.exeorwscript.exe
🧬 Loader Execution
- Encoded PowerShell script is downloaded from a C2 server
- Uses
Invoke-Expression (IEX)to dynamically decode and run payload in memory - Deploys Remcos RAT via a reflective PE injection technique or direct shellcode execution
🧠 No Files, No Trace
- No executable or DLL is dropped to disk
- Registry and WMI may be used for persistence, but payload never touches the file system
Technical Analysis of the PowerShell Loader
The loader uses layered obfuscation and anti-analysis tactics:
🧪 Script Structure
- Base64 and Gzip compression used to hide payload
- Strings are chunked and concatenated at runtime to avoid signature-based detection
- Entropy levels are manipulated to evade sandbox entropy scoring heuristics
🔒 Evasion Techniques
- Environment checks (
Get-WmiObject Win32_ComputerSystem) - Anti-sandbox delays using
Start-SleepandMeasure-Command - No hardcoded IOCs—C2 fetched dynamically via remote PowerShell commands (e.g., using
Invoke-WebRequest)
⚙️ Execution Flow
$enc = "H4sIAAAAAAA..."; $dec = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($enc)); IEX $dec
This form avoids detection by static analysis tools and allows the loader to update its payload logic in real time.
Remcos RAT Capabilities and Persistence Techniques
Once loaded in memory, Remcos RAT performs:
💻 Core Capabilities
- Keylogging, screen capturing, clipboard spying
- File browser and exfiltration tools
- Remote shell, process injection, and credential dumping
- Microphone and webcam access
🧷 Persistence
- If persistence is configured, techniques may include:
- WMI Event Subscription
- Registry Run keys
- Scheduled Tasks created via
schtasks.exefrom within PowerShell context - However, the campaign variant reviewed in this attack avoided persistence to further reduce footprint
Detection and Mitigation Strategies
🔍 Detection
- Monitor for PowerShell child processes spawned by Office or browser processes (e.g.,
WINWORD.exe → powershell.exe) - Look for network activity from PowerShell making HTTP requests (
User-Agentanomalies, base64 in URLs) - Detect use of LOLBins executing script content, especially
mshta.exe,wscript.exe, andregsvr32.exe
🛡️ Mitigation
- Disable PowerShell v2.0 and enforce Constrained Language Mode
- Use AppLocker or WDAC to restrict LOLBin usage
- Enable Script Block Logging and Module Logging in PowerShell
- Segment network to isolate user endpoints from critical infrastructure
- Utilize behavioral EDRs that detect in-memory threats (e.g., reflective PE injections, LSASS access attempts)
YARA Rules, IOCs, and PowerShell Artifacts
🧬 YARA Sample
rule Remcos_PowerShell_Loader {
meta:
description = "Detects base64-encoded PowerShell with Invoke-Expression"
strings:
$ps1 = /[Ii]nvoke\-Expression\s+\(\s*\[System\.Text\.Encoding\]/
$b64 = /[A-Za-z0-9+\/]{100,}={0,2}/
condition:
$ps1 and $b64
}🧷 Indicators of Compromise (IOCs)
- C2 Domains:
hxxp://stealth-update[.]com/apihxxps://remcos-support[.]xyz/psloader- Registry Paths:
HKCU:\Software\Microsoft\Windows\CurrentVersion\Run\RemcosShell- WMI subscription to
__EventFilteronWin32_LocalTime
Conclusion: Securing Against Fileless RAT Threats
This campaign proves how PowerShell-based loaders can deploy Remcos RAT in fully fileless attacks, leveraging LOLBins and memory injection to avoid traditional detection. As organizations rely more on cloud-delivered endpoints and browser-based workflows, fileless malware will continue to rise.
Security teams must harden PowerShell environments, monitor for behavior-based indicators, and extend defenses to include in-memory threat detection and real-time script analysis.
Organizations without visibility into script execution and child process behavior are flying blind in the face of modern, stealthy threats like this one.