Threat actors use SMS and voice deepfakes to impersonate US officials, targeting citizens and enterprises. Learn how to detect and mitigate this rising threat.
Overview of Deepfake Impersonation Threat
In a sharp escalation of social engineering tactics, cybercriminals are now impersonating U.S. government officials using a combination of SMS phishing and AI-generated voice deepfakes. These attacks aim to manipulate victims into divulging sensitive data, installing malware, or transferring money under the false pretense of law enforcement or government activity.
The trend underscores the convergence of synthetic media, smishing (SMS phishing), and voice cloning, presenting a complex, multi-channel threat that traditional security controls often fail to detect.
Tactics: SMS Phishing Meets Voice Deepfakes
The attacks are structured in a two-stage deception process:
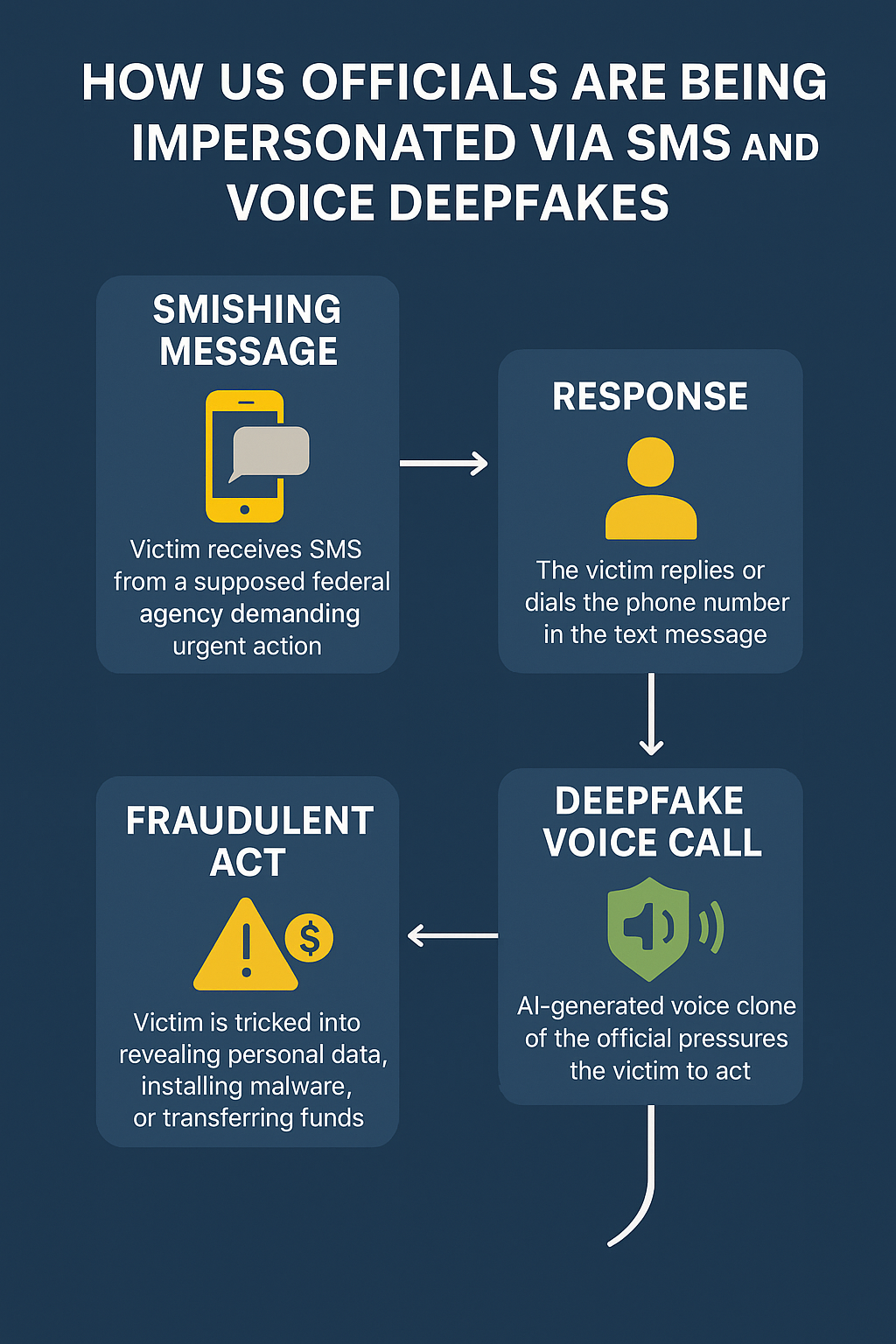
- SMS Hook (Smishing):
- Victims receive a text claiming to be from a federal agency such as the IRS, SSA, DHS, or even FBI.
- The message often references fabricated investigations, benefits issues, or court appearances.
- It includes a callback number or a prompt to reply.
- Voice Deepfake Callback:
- If victims respond, they receive a call from a synthetic voice clone trained on real audio from known officials.
- These AI-driven voices are highly convincing, incorporating real cadence, tone, and even accent.
- The call then pressures victims to act (e.g., “verify identity”, “avoid legal action”).
This hybrid approach is designed to bypass text-only filters and exploit trust in official-sounding voices.
Who Was Targeted and Why It Matters
Initial reports confirm the following victim categories:
- Elderly individuals, often targeted with fear-based language
- Government contractors and federal employees, where attackers attempted data exfiltration
- Citizens with public LinkedIn profiles referencing work with defense or federal programs
The impersonated officials include:
- Federal law enforcement officers
- IRS agents
- State-level health and benefits department staff
The attackers’ objectives varied from identity theft and wire fraud to corporate espionage and information gathering.
Technical Analysis: Deepfake Voice Pipeline
The attackers employed TTS (text-to-speech) models fine-tuned on real voice samples obtained from:
- YouTube interviews
- Public press releases
- Government briefings
Probable tools used in the threat actor’s pipeline:
- ElevenLabs, Resemble.ai, or open-source alternatives like Coqui TTS
- Real-time audio playback tools (Voicemod, OBS scripting, customized SIP softphones)
- VoIP/SIP infrastructure with spoofed caller IDs
Synthetic voice models were enhanced using AI noise filters to simulate real phone call conditions.
Real-World Attack Flow
graph TD
A[SMS Smishing Campaign] --> B[Victim Clicks or Replies]
B --> C[Receives AI-generated Callback]
C --> D[Deepfake Voice Claims Urgent Action Required]
D --> E{Victim Responds?}
E -- Yes --> F[Credential Theft / Funds Transfer / Malware Drop]
E -- No --> G[Attack Ends or Retargets]
Indicators of Compromise (IOCs) and Behaviors
SMS/Voice-Based IOCs:
- Caller ID spoofing from “official” government numbers
- Callback numbers using VoIP with no traceable records
- Messages referencing fake “case IDs”, “legal notices”, or “urgent identity verification”
Behavioral Indicators:
- Calls made outside of federal agency hours (e.g., Sunday evenings)
- Scripts demanding real-time actions under time pressure
- Victim-reported uncanny tone in voice (too perfect or lacking natural pauses)
Enterprise Risks and Recommended Defenses
Risks:
- Social engineering of staff using trusted voice authority
- Credential phishing in hybrid work environments
- Use of victim devices to pivot into enterprise networks
Defenses:
- Implement inbound voice verification policies for employees
- Train staff on audio deepfake awareness and media literacy
- Use voiceprint biometric validation where feasible for sensitive communications
- Deploy mobile security solutions that scan SMS and VoIP channels
- Enable anomaly-based alerting for unusual outbound communications
Strategic Response and Policy Implications
This wave of deepfake attacks highlights the urgent need for policy modernization:
- Stronger regulation of AI-based synthetic voice tools
- Mandating caller ID authentication protocols like STIR/SHAKEN
- Establishing a federal notification system for known impersonation threats
- Funding cross-sector deepfake detection research
Public-private collaboration must intensify to mitigate these AI-driven impersonation threats, which will only grow more convincing with time.
Conclusion
The impersonation of US officials via SMS and AI-generated voice calls signals a chilling evolution in social engineering. As synthetic media tools become commoditized, threat actors are weaponizing trust and authority itself.
It is now critical that both individuals and organizations adopt proactive defenses—not just technical controls, but awareness, verification processes, and cross-channel detection capabilities.
